|
2578-1669 (Online) Journal Abbreviation: Comput. Soft. Media. Appl. |
Computer Software and Media Applications (CSMA) is a peer-reviewed, open-access publication that delivers high-quality journal papers that are significant in all disciplines of computer software and media applications. With a focus on publishing high quality academic papers, detailing the latest information and research in the field of computer software and media applications. CSMA aims to provide a communication and information exchange platform for a broad audience of professionals. Articles from related fields that are interesting to a broad readership are particularly welcome. |
Online Submissions
Registration and login are required to submit items online and to check the status of current submissions.
Already have a Username/Password for Computer Software and Media Applications?
GO TO LOGIN
Need a Username/Password?
GO TO REGISTRATION
Submission Preparation Checklist
As part of the submission process, authors are required to check off their submission's compliance with all of the following items, and submissions may be returned to authors that do not adhere to these guidelines.
- The submission has not been previously published, nor is it before another journal for consideration (or an explanation has been provided in Comments to the Editor).
- The submission file is in Microsoft Word format.
- Where available, URLs for the references have been provided.
- The text adheres to the stylistic and bibliographic requirements outlined in the Author Guidelines, which is found in About the Journal.
- If submitting to a peer-reviewed section of the journal, the instructions in Ensuring a Blind Review have been followed.
Privacy Statement
The names and email addresses entered in this journal site will be used exclusively for the stated purposes of this journal and will not be made available for any other purpose or to any other party.
Article Processing Charges (APCs)
Computer Software and Media Applications is an Open Access Journal under EnPress Publisher. All articles published in Computer Software and Media Applications are accessible electronically from the journal website without commencing any kind of payment. In order to ensure contents are freely available and maintain publishing quality, Article Process Charges (APCs) are applicable to all authors who wish to submit their articles to the journal to cover the cost incurred in processing the manuscripts. Such cost will cover the peer-review, copyediting, typesetting, publishing, content depositing and archiving processes. Those charges are applicable only to authors who have their manuscript successfully accepted after peer-review.
| Journal Title | APCs |
|---|---|
| Computer Software and Media Applications | $800 |
We encourage authors to publish their papers with us and don’t wish the cost of article processing fees to be a barrier especially to authors from the low and lower middle income countries/regions. A range of discounts or waivers are offered to authors who are unable to pay our publication processing fees. Authors can write in to apply for a waiver and requests will be considered on a case-by-case basis.
APC Payment
Payments for APC of this journal can be made through our online PayPal payment gateway. Enter the article no. into the below textbox and select "Pay Now" to proceed with payment.
*Article No. is mandatory for payment and it can be found on the acceptance letter issued by the Editorial Office. Payment without indicating Article No. will result in processing problem and delay in article processing. Please note that payments will be processed in USD. You can make payment through Masters, Visa or UnionPay card.
Vol 8, No 1 (2025)
Table of Contents
Artificial intelligence-empowered music processing is a domain that involves the use of artificial intelligence technologies to enhance music analysis, understanding, and generation. This field encompasses a variety of tasks from music generation to music comprehension. In practical applications, the complexity of interwoven tasks, differences in data representation, scattered distribution of tool resources, and the threshold of professional music knowledge often become barriers that hinder developers from smoothly carrying out generative tasks. Therefore, it is essential to establish a system that can automatically analyze their needs and invoke appropriate tools to simplify the music processing workflow. Inspired by the recent success of Large Language Models (LLMs) in task automation, we have developed a system named LongMergent, which integrates numerous music-related tools and autonomous workflows to address user requirements. By granting users the freedom to effortlessly combine tools, this system provides a seamless and rich musical experience.
Announcements
ESEM '22 will be held in New York |
|
 |
|
| Posted: 2022-08-08 | More... |
IBM Announces New AIOps Solutions Designed to Automate Software License Compliance |
|
 |
|
| Posted: 2022-03-26 | More... |
The epidemiological impact of the NHS COVID-19 app |
|
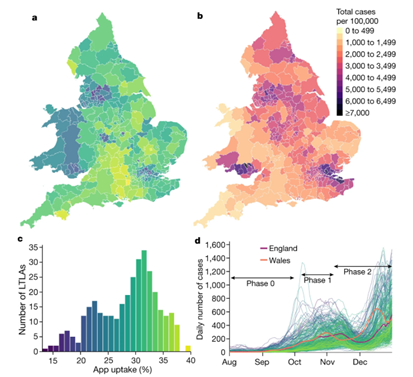 @Chris Wymant, et al. Figure1. Geographical variability of app uptake and cases of COVID-19. |
|
| Posted: 2021-06-08 | More... |
| More Announcements... |










 ISSN:
ISSN: Open Access
Open Access
